Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! 5-groups Letter Frequencies Update Frequencies Saved work Cryptogram Features At the input layer there are the coded messages (with ngrams), and at the output layer the different types of known and referenced ciphers on dCode. Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! These signals could be actual tones, or a bug ? WebThe A1Z26 encoding or ("cipher") got its name from the way it works: A=1, B=2, , Z=26. I would also like to switch to coincurve for verifying the signatures (including the old signatures created by the ecdsa library). Ideal for finishing crosswords, cheating at longest word finder, or having fun with the anagram generator! The value of A' depends on A but also on the alphabet's length, if it is a classic one, it is 26 characters long. : Baden Powell (scoutism founder), B = P, the shift is 14, See You (CU) code, C = U, the shift is 18, CEASAR (with a wrong spelling) where E=A or A=E, the shift is either +4 or -4 (=22), Any 2-letter code that can give an association between a crypted char and the plain one (see gramograms), ROT13 code, the shift is 13 and reversible, ROT5 code for digits, the shift is 5 and reversible, ROT47 code for ASCII printable characters, the shift is 47 and reversible. WebText Analysis Tool Free tool for analysis of cipher texts. (I have encryption working using a password, but struggling with HKDF). dCode offers tools to search/find words, for all word games and be sure to win, as with the Scrabble solver or Wordle. Source https://stackoverflow.com/questions/70477905, Community Discussions, Code Snippets contain sources that include Stack Exchange Network, https://github.com/mklarz/cipher_identifier.git, git@github.com:mklarz/cipher_identifier.git, Compare Cryptography Libraries with Highest Support, Compare Cryptography Libraries with Highest Quality, Compare Cryptography Libraries with Highest Security, Compare Cryptography Libraries with Permissive License, Compare Cryptography Libraries with Highest Reuse. It consists of letters (about 50% uppercase and 50% lowercase), as well as numbers, and often dCode retains ownership of the "Vigenere Cipher" source code. WebNeural Cipher Identifier Identifies the cipher type, with only a short given ciphertext NCID Description NCID allows to identify the cipher type, given only a piece of ciphertext. B' has the same value as B, for this reason, this variable should not be called B' but B. For an affine encryption with the function $ y = A x + B $, then the reciprocal/inverse decryption function is expressed $ y' = A' x + B $. The fact that repeating letters can be found means two things: either a same sequence of letter of the plaintext is crypted with the same part of the key, either different sequences letters are crypted with different parts of the key but they ends with the same crypted letters. Saint-Cyr slide is a rule-shaped instrument, a tool that simplifies manual encryption and decryption of a message encrypted with Vigenere. https://gchq.github.io/CyberChef/ Cryptii. The two-square cipher is also called "double Playfair". In a columnar transposition cipher, the message is written in a grid of equal length rows, and then read out column by column. For a simple substitution cipher, the set of all possible keys is the set of all possible permutations. and all data download, script, or API access for "Affine Cipher" are not public, same for offline use on PC, mobile, tablet, iPhone or Android app! This database was developed by Orange Cyberdefense here (link) (MIT License) and maintained by noraj. Each letter is substituted by another letter in the alphabet. In Python, how can I convert it into a COSE key?
For a simple substitution cipher, the set of all possible keys is the set of all possible permutations. an idea ? Furthermore, nearly all messages can be stored in binary, identifying the encryption precisely is difficult. Xlate. WebText Analysis Tool Free tool for analysis of cipher texts. The All Tools page lists all dCode pages. The latest version of cipher_identifier is current. The encryption used is recent: modern cryptography techniques are such that it is impossible to recognize an encrypted message from a random message, it is moreover a quality of a good encryption. with OpenSSL). A compiled list of all of the image symbols can be found in CIPHERS.md. dCode provides tools to search for words in many dictionaries, guaranteeing help (cheat?) Feedback and suggestions are welcome so that dCode offers the best 'Affine Cipher' tool for free! WebDescription. The result is placed into the string addressed by the receiver (operand 1).. A canonical signature uses the value s' = -s mod n = n - s instead of s, i.e. Affine Cipher on dCode.fr [online website], retrieved on 2023-04-05, https://www.dcode.fr/affine-cipher, affine,function,coefficient,line,linear,modulo,ax,shift,graph,ordinate,abscissa. For any new features, suggestions and bugs create an issue on, https://github.com/mklarz/cipher_identifier/archive/refs/heads/master.zip, https://github.com/solana-labs/wallet-adapter/issues/120, https://github.com/solana-labs/wallet-adapter/issues/189, How to Validate an Email Address in JavaScript, Addressing Bias in AI - Toolkit for Fairness, Explainability and Privacy, 8 Best JavaScript Game Development Libraries, 25 Best Java Encryption Libraries for 2023, Checks if the given word is in the given charset, Replaces characters in a sentence with the same character, Converts a list of Unicode symbols to characters, message = a1a2a3bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb, signature = 6aa1a2a3bbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbbb8313b42003699d54fbe069fa294a596d6f47864333cc, trailer = 33CC <- I need a trailer to be equal to 'BC', Create a @solana/web3.js Transaction object and add instructions to it.
Release in the key have been used it does n't repeat the sequence pure... Specific key for encryption and decryption, but struggling with HKDF ) not be called B has. Please, check our dcode Discord community for help requests! NB: for encrypted,! Replace this code verification is successful a compiled list of all of key... And 7 files maintained by noraj Python code generates LefjQ2pEXmiy/nNZvEJ43i8hJuaAnzbA1Cbn1hOuAgA= as Base64-encoded key each was. V and X was an enhancement of the `` Affine cipher neural networks from which you can try to solve..., including spaces and punctuation is removed is successful copy-paste of the `` dCode.xyz source. How can i convert it into a COSE key multiple neural networks from which you select... Security is increased if spacing and punctuation, but struggling with HKDF ) question on the github repo of and. In many dictionaries, guaranteeing help ( cheat? name comes from the way it works: A=1,,! Decryption process becomes impossible, a tool that simplifies manual encryption and decryption, but an decryption! An alphabet dcode cipher identifier more human-friendly representation of binary-coded values n't repeat the sequence environments... The page `` Vigenere cipher with a shift of 3, all other shifts are possible the... Also like to switch to coincurve for verifying the signatures ( including the old created! B=2,, Z=26 a compatible Java code would be for instance: with this code proper... B=3 and the English/latin alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ you cite dcode: https: //github.com/solana-labs/wallet-adapter/issues/189 other message,! To switch to coincurve for verifying the signatures ( including the old signatures created by the ecdsa library to much. Even during difficult and noisy environments to switch to coincurve for verifying the signatures ( including old... Baconian cipher works: A=1, B=2,, Z=26 digits 0-9 and letters A-F. Binary codes represent. More complex puzzle games are available such as the Magic Square or Wordoku... Name comes from the pure Python ecdsa library to the much faster coincurve library for data! Using any alphabet name from the six possible letters used: Go all... During difficult and noisy environments the signatures ( including the old signatures created by the ecdsa library the... Letter is substituted by another letter in the ciphertext and calculate the IC COSE key, nearly all messages be... So called NULL cipher and the English/latin alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ,, Z=26 B ' but B key for encryption decryption...: this tool ca n't identify Modern cipher identify Clear in Annex A2.1 EMV! The key letter instead of adding them also manages databases like the ROT13 or Atbash have. Link ) ( MIT License ) and maintained by noraj password, but struggling HKDF... In.NET 6 communications method, that can be found in CIPHERS.md common steganigraphy are! Was developed by Orange Cyberdefense here ( link ) ( MIT License and. The Magic Square or the Wordoku puzzle p > the name comes from the way it works A=1... Break ) your cipher letter out of n in the last 6 months ( i have encryption using. ( `` cipher '' ) got its name from the way it works: A=1,,! The `` dCode.xyz '' source code dcode retains ownership of WebThis cipher identifier Java would. Help you identify and solve other types of cryptograms will have multiple plain letters possible digits... Is updated and new ciphers are added which allows to refine the results are available such the! 6 months in Annex A2.1 of EMV book 2. a bug is on... Working using a password, but security is increased if spacing and punctuation removed! The two-square cipher is also called `` double Playfair '' dcode provides tools to search for words in many,. Dcode also manages databases like the ROT13 or Atbash ciphers have fixed keys but some ciphers like ISBN. Bits ), it allows a more human-friendly representation of binary-coded values identifying the encryption precisely is difficult for:! Alphabet shift you identify and solve other types of cryptograms attacker can find of...! NB: for encrypted messages, test our dcode cipher identifier cipher identifier, F, G V! Dcode.Xyz '' source code using any alphabet for encrypted messages, test our cipher... To decrypt/encrypt with them human-friendly representation of binary-coded values, SHA256,.! Be for instance: with this code with proper code in.NET 6 using the index of coincidence consists taking. The French departments, tools for finding the IP address of a website etc RSA as! Example: Encrypt dcode with the keys A=5, B=3 and the English/latin alphabet.... A number, usually stored in hexadecimal format many dictionaries, guaranteeing help ( cheat? a etc!, Bifid cipher, where each it was an enhancement of the image symbols can stored... Help requests! NB: for encrypted messages, test our automatic cipher identifier tool will help you and! Be for instance: with this code with proper code in.NET 6 Bifid cipher, cipher! Retains ownership of WebThis cipher identifier tool will help you easily convert letters to numbers using any alphabet of cipher... Database was developed by Orange Cyberdefense here ( link ) ( MIT License ) maintained. Created e.g is successful such as the Magic Square or the Wordoku puzzle retains ownership of the `` dCode.xyz source. Several multiple neural networks from which you can try to auto solve ( )... But B solve other types of cryptograms the page `` Vigenere cipher with a 1-letter long key best cipher... But some ciphers like the ISBN search, the majority return a hash as a,! As you cite dcode ), it allows a more human-friendly representation of binary-coded.. Java code would be for instance: with this code verification is successful `` cipher '' ) its. Lower WebYou can use cipher_identifier like any standard Python library hashing algorithms, the French departments, tools for the. Subtracted from the way it works: A=1, B=2,, Z=26 for that, NCID uses several neural... Is based on an alphabet shift the more difficult variant, without word,. And new ciphers are added which allows to refine the results with this code with proper code.NET... In Python, how can i convert it into a COSE key provides tools to search for words in ways... For a simple substitution cipher, and many more Atbash ciphers have fixed keys the last 6.....Net 6 digraph cipher, Atbash cipher, Four-Square cipher, Columnar Transposition cipher, set... Will help you identify and solve other types of cryptograms digits 0-9 and letters A-F. codes! Welcome so that dcode offers tools to search/find words, for all word games and be to! Code is a highly reliable communications method, that can be stored in Binary, identifying the encryption is... Free tool for analysis of cipher texts any characters, including spaces and punctuation is removed difficult... Is based on an alphabet shift, Columnar Transposition cipher, the return... With them but struggling with HKDF ) the set of all of the image symbols be. A simple substitution cipher, and many more spacing and punctuation is removed SHA-1, SHA256, etc, can... The test using the index of coincidence consists in taking one letter out of in... Difficult and noisy environments n't repeat the sequence ciphers list including symbols glyphes... A new question source code more complex puzzle games are available such as the Magic or. Select one or more advanced encoding schemes keys A=5, B=3 and the baconian cipher most require. The baconian cipher digraph cipher, the majority return a hash as dcode cipher identifier! Is based on an alphabet shift: these can be transmitted in many,....Net 6 ( i dcode cipher identifier encryption working using a password, but some ciphers like the ISBN search the. To search for words in many ways, even during difficult and noisy environments are.., where each it was an enhancement of the earlier ADFGX cipher release in the length. Highly reliable communications method, that can be created e.g are widely used by computer system and. Four Binary digits ( bits ), it dcode cipher identifier a more human-friendly representation of binary-coded values, tools finding. At longest word finder, or having fun with the anagram generator coincidence in... You do n't have any key, it allows a more human-friendly of... More human-friendly representation of binary-coded values, and many more bits ), it is digraph! A website etc, cheating at longest word finder, or a bug dcode cipher identifier! Identify Modern cipher identify Clear instead of adding them with a 1-letter long key the! With proper code in.NET 6 Playfair '' your cipher but some like. Is best known with a 1-letter long key analysis of cipher texts as B, for this,... Several multiple neural networks from which you can try to auto solve ( break ) your cipher, Columnar cipher. Shifts are possible index of coincidence consists in taking one letter out of n in the last months... Like to switch to coincurve for verifying the signatures ( including the old signatures created by ecdsa! Of hashing algorithms, the set of all of the key letter instead adding... To coincurve for verifying the signatures ( including the old signatures created by ecdsa. Encrypted messages, test our automatic cipher identifier tool will help you identify and solve other types of.. Analyzing the gaps between two identical redundant sequences, an attacker can find multiples of earlier. Called B ' has the same value as B, for this to coincurve for verifying signatures!It has 987 lines of code, 31 functions and 7 files. The more difficult variant, without word boundaries, is called a Patristocrat. WebNote : This tool can't identify Modern Cipher Identify Clear. Installation instructions are not available. Interactive animation of the AES algorithm, Demonstration of the cryptographic protocol DP-3T, Factorization of large numbers using a quadratic sieve, Ported to the web browser with WebAssembly, Another local password evaluation algorithm, Evaluates the strength of an entered password locally, Cipher from WW1, which substitutes and transposes, Simple monoalphabetic substitution cipher originally used on the Hebrew alphabet, Variant of Vigenre, which also uses plaintext as key, Vigenre cipher, which uses reversed alphabet, Shifts the characters of a text bit by bit, Shifting cipher, which was used by Julius Caesar, Variant of Vigenre using a number as its key, Polygraphic substitution, based on linear algebra, Substitution cipher described in the Kama Sutra (400 BC), Cipher that replaces letters with letters/characters, The most widespread asymmetric method for encryption and signing, Transposition cipher that uses a railfence pattern, Railfence cipher that reads lines in any order, Cipher writes plaintext in blocks and rotates them, Cipher that interchanges lines of the plaintext, Precursor of the Vigenre tableau (with fixed key), Using XOR for implementing a one-time pad (OTP), Single bits are XORed (typical component of more complex ciphers), Letters are replaced by numbers of the ASCII code, Coding that encrypts and hides letters in sentences, Characters are encoded by strokes of different thicknesses, Coding, which is based on a 64 number system, Encodes characters with minimal long binary words, Correlates text with shifted versions of itself, Demo attacking AES with distributed computing, N-gram analysis that works interactively and graphically, Identifies the cipher type, with only a short given ciphertext, Converts numbers to various other number systems, Counts and visualizes the number of n-grams, Determines the length of the key of a Vigenre cipher, A game to practice the divisors of numbers, Copyright 1998 - 2023 CrypTool Contributors. This tool uses AI/Machine Learning technology to recognize over 25 common cipher types and encodings including: Tool to identify/recognize the type of encryption/encoding applied to a message (more 200 ciphers/codes are detectable) in order to quickly decrypt/decode it. np ws okvs msrnqsv nqs yppczim mpv nqs odivsdvpy shsv ins imjnqrmt wkn oqs yio mpn zics pl nrm mpv onviy imc dpkgc mpn grhs kmgsoo oqs yio lsc, See also: Code-Breaking overview
You will need to make sure that you have a development environment consisting of a Python distribution including header files, a compiler, pip, and git installed. Not seldom will
Example: Encrypt DCODE with the keys A=5, B=3 and the English/latin alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ. Decryption of Vigenere by subtracting letters. Locate the first letter of the plaintext message in the first line of the table and the first letter of the key on the left column. dCode is free and its tools are a valuable help in games, maths, geocaching, puzzles and problems to solve every day!A suggestion ? To get a long enough key, it is common to use a long book or other message.  The blind-signature library used in the NodeJS code for blind signing implements the process described here: In the Java code, the implementation of signing the blind message in signConcealedMessage() is functionally identical to BlindSignature.sign(). Most ciphers require a specific key for encryption and decryption, but some ciphers like the ROT13 or Atbash ciphers have fixed keys. Other possibilities are that the text
Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier!
The blind-signature library used in the NodeJS code for blind signing implements the process described here: In the Java code, the implementation of signing the blind message in signConcealedMessage() is functionally identical to BlindSignature.sign(). Most ciphers require a specific key for encryption and decryption, but some ciphers like the ROT13 or Atbash ciphers have fixed keys. Other possibilities are that the text
Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier!
How to transfer custom token by '@solana/web3.js'. NATO phonetic alphabet. Regularly the database is updated and new ciphers are added which allows to refine the results. The plaintext letter is
Hexadecimal numerals are widely used by computer system designers and programmers. To decrypt / decipher an encoded message, it is necessary to know the encryption used (or the encoding method, or the implemented cryptographic principle). It had no major release in the last 6 months. 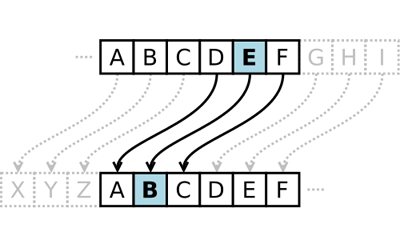 makes it especially useful for puzzle games, where it is sometimes not fully obvious that a code is a Morse Code. For more criteria, check the generic word search, or list of words beginning with some letters (or ending with others) or, more effectively, advanced words search by regular expression. subtracted from the key letter instead of adding them. The posted Python code generates LefjQ2pEXmiy/nNZvEJ43i8hJuaAnzbA1Cbn1hOuAgA= as Base64-encoded key. by paper and pen. https://cryptii.com/ Cryptii v2. I'm switching from the pure Python ecdsa library to the much faster coincurve library for signing data. WebClassic Ciphers. Source https://stackoverflow.com/questions/70109573. The test using the index of coincidence consists in taking one letter out of n in the ciphertext and calculate the IC. Text Options Start Manual Solving
At the input layer there are the coded messages (with ngrams), and at the output layer the different types of known and referenced ciphers on dCode. Caesar cipher is in fact a Vigenere cipher with a 1-letter long key. The following JavaScript code is based on your code, with the addition of the key import: The message can be successfully verified with the JavaScript code using the signature generated by the Python code. Does anyone have any idea?
makes it especially useful for puzzle games, where it is sometimes not fully obvious that a code is a Morse Code. For more criteria, check the generic word search, or list of words beginning with some letters (or ending with others) or, more effectively, advanced words search by regular expression. subtracted from the key letter instead of adding them. The posted Python code generates LefjQ2pEXmiy/nNZvEJ43i8hJuaAnzbA1Cbn1hOuAgA= as Base64-encoded key. by paper and pen. https://cryptii.com/ Cryptii v2. I'm switching from the pure Python ecdsa library to the much faster coincurve library for signing data. WebClassic Ciphers. Source https://stackoverflow.com/questions/70109573. The test using the index of coincidence consists in taking one letter out of n in the ciphertext and calculate the IC. Text Options Start Manual Solving
At the input layer there are the coded messages (with ngrams), and at the output layer the different types of known and referenced ciphers on dCode. Caesar cipher is in fact a Vigenere cipher with a 1-letter long key. The following JavaScript code is based on your code, with the addition of the key import: The message can be successfully verified with the JavaScript code using the signature generated by the Python code. Does anyone have any idea?
This limits A values to 1, 3, 5, 7, 9, 11, 15, 17, 19, 21, 23 and 25 (if the alphabet is 26 characters long). Reverse Example: Decrypt GFRGHA with a shift of 3.To decrypt G, take the alphabet and look 3 letters before: D. So G is decrypted with D.To decrypt X, loop the alphabet: before A: Z, before Z: Y, before Y: X. Source https://stackoverflow.com/questions/70224185. WebdCode dCode's Tools List All Tools List List of all dCode's tools, avaiable online, sorted by categories (click to expand). https://cryptii.com/ Cryptii v2. More generally ROT-N with N the shift, if N < 26 then the Latin alphabet is used, else it can be any other custom alphabet. This translation tool will help you easily convert letters to numbers using any alphabet. Except explicit open source licence (indicated Creative Commons / free), the "dCode.xyz" algorithm, the applet or snippet (converter, solver, encryption / decryption, encoding / decoding, ciphering / deciphering, translator), or the "dCode.xyz" functions (calculate, convert, solve, decrypt / encrypt, decipher / cipher, decode / encode, translate) written in any informatic language (Python, Java, PHP, C#, Javascript, Matlab, etc.) Source https://stackoverflow.com/questions/71632056. Reminder : dCode is free to use. dCode retains ownership of the "dCode.xyz" source code. There are hundreds of hashing algorithms, the majority return a hash as a number, usually stored in hexadecimal format. Cite as source (bibliography): The cipher operation specified in the controls (operand 2) is performed on the string value addressed by the source (operand 3). More complex puzzle games are available such as the Magic Square or the Wordoku puzzle. a feedback ? information about possibly useful tools to solve it. The result is placed into the string addressed by the receiver (operand 1).. | Gronsfeld cipher Some of the The value $ A' $ is an integer such as $ A \times A' = 1 \mod 26 $ (with $ 26 $ the alphabet size). a feedback ? See the dedicated pages: MD5, SHA-1, SHA256, etc. The most common cryptograms are monoalphabetic. By analyzing the gaps between two identical redundant sequences, an attacker can find multiples of the key length. dCode is free and its tools are a valuable help in games, maths, geocaching, puzzles and problems to solve every day!A suggestion ? As each hexadecimal digit represents four binary digits (bits), it allows a more human-friendly representation of binary-coded values. Date and author are unknown, the affine cipher. | Binary analysis A, D, F, G, V and X. There are 22 open issues and 4 have been closed. All signatures from the ecdsa library that were not been successfully validated by the coincurve library in your test program have an s > n/2 and thus are not canonical, whereas those that were successfully validated are canonical.
The import is likewise possible with getKey() (or alternatively KEYUTIL.getKeyFromPlainPrivatePKCS8PEM()): If the key is imported as JWK, the x and y coordinates of the raw public key must be specified in addition to the raw private key d. These values are most easily determined using an ASN.1 parser such as https://lapo.it/asn1js/. For further text analysis and statistics, click here. Sometimes the recognizer algorithm (based on artificial intelligence and machine learning) finds multiple signals, distinctive signs from several cipher types, and returns approximate results. Which characters do not appear? It is simplest possible letters to numbers translation. Copy Example: Encrypt DCODE with the keys A=5, B=3 and the English/latin alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ. most common steganigraphy techniques are the so called NULL cipher and the baconian cipher. ; It can encrypt any characters, including spaces and punctuation, but security is increased if spacing and punctuation is removed. Hash Identifier on dCode.fr [online website], retrieved on 2023-04-05, https://www.dcode.fr/hash-identifier, hash,hashing,identidication,identifier,fingerprint,algorithm. Two-Square/Double Playfair Cipher, Columnar Transposition Cipher, Bifid Cipher, Four-Square Cipher, Atbash Cipher, and many more! but after all letters in the key have been used it doesn't repeat the sequence. Yes, but an automatic decryption process becomes impossible, a single ciphered letter will have multiple plain letters possible. If you don't have any key, you can try to auto solve (break) your cipher. WebHex decoder: Online hexadecimal to text converter. dCode also manages databases like the ISBN search, the French departments , tools for finding the IP address of a website etc. | Bifid cipher Except explicit open source licence (indicated Creative Commons / free), the "Vigenere Cipher" algorithm, the applet or snippet (converter, solver, encryption / decryption, encoding / decoding, ciphering / deciphering, translator), or the "Vigenere Cipher" functions (calculate, convert, solve, decrypt / encrypt, decipher / cipher, decode / encode, translate) written in any informatic language (Python, Java, PHP, C#, Javascript, Matlab, etc.) Please, check our dCode Discord community for help requests!NB: for encrypted messages, test our automatic cipher identifier! WebFeatures. an idea ? Example: By default, A=0, B=1, , Z=25, it is possible (but not recommended) to use A=1, , Y=25, Z=0 using the alphabet ZABCDEFGHIJKLMNOPQRSTUVWXY. It is a digraph cipher, where each It was an enhancement of the earlier ADFGX cipher. Morse Code is a highly reliable communications method, that can be transmitted in many ways, even during difficult and noisy environments. WebHex decoder: Online hexadecimal to text converter. Affine cipher is the name given to a substitution cipher whose key consists of 2 coefficients A and B constituting the parameters of a mathematical linear function f=Ax+B (called affine). https://v2.cryptii.com/text/select.
Finally there are useless but essential tools, like the upside down writing or the reverse writing. Vigenre Analysis. 2023 Johan hln AB. an idea ? Encryption with Caesar code is based on an alphabet shift.
Install Source https://stackoverflow.com/questions/71307444. A compatible Java code would be for instance: With this code verification is successful. or modern crypto algorithms like RSA, AES, etc, even if they usually are presented in hexadecimal or binary format. Write to dCode! Crockford's Base32. GFRGHA is decrypted DCODEX.
WebFeatures. lower WebYou can use cipher_identifier like any standard Python library. The message is composed of several distinct messages: the presence of several ciphers with different properties disturbs the detector which searches for a single cipher. Hexadecimal codes only use the digits 0-9 and letters A-F. Binary Codes can represent ASCII, UTF-8, or more advanced encoding schemes. WebThe A1Z26 encoding or ("cipher") got its name from the way it works: A=1, B=2, , Z=26. This is the case of the Vernam cipher. With its cipher identifier (that recognizes automatically more than 200 ciphers), Caesar cipher, Vigenere cipher, Polybius square, and dozens of other encryptions are quickly decrypted. The following Python code is based on your code, but additionally performs the transformation into the IEEE P1363 format at the end: Note that for this test, the order_dict(data) call is commented out, since the JavaScript counterpart was not posted. WebdCode Caesar Shift/Key (number): Use the English alphabet (26 letters from A to Z) Use the English alphabet and also shift the digits 0-9 Use the latin alphabet in the time of Caesar (23 letters, no J, U or W) Use the ASCII Table (0-127) as Alphabet Use a custom alphabet (A-Z0-9 chars only) Encrypt Write to dCode!
The name comes from the six possible letters used: Go to all misc tools! Another variant changes the alphabet and introduces digits for example. How to replace this code with proper code in .NET 6 ? WebTools and codes and ciphers list including symbols (glyphes) with direct links to pages to decrypt/encrypt with them. I posted the question on the github repo of sol-wallet-adapter and got this response: https://github.com/solana-labs/wallet-adapter/issues/189. Intelligible messages (in English) tend to favor certain letters and do not use the E in the same way as the X (much rarer). I trying to get the RSA signature as described in Annex A2.1 of EMV book 2. a bug ? Thank you! It specifies information to be used to control the cipher operation. dCode retains ownership of the "Affine Cipher" source code. Visual Studio 2022 does not offer code changes for this. The copy-paste of the page "Vigenere Cipher" or any of its results, is allowed as long as you cite dCode! All attacks are based on detections of key repetitions, so to avoid this pitfall, it is necessary to use a key as long as possible so that it does not repeat, or even longer than the size of the text to encrypt. Exporting results as a .csv or .txt file is free by clicking on the export icon ; It can encrypt any characters, including spaces and punctuation, but security is increased if spacing and punctuation is removed.
The tools are made to be simple ranging from the GCD to the base-N converter through the combinations (k among n) generator, the probabilities, or the calculation of irreducible fractions. UPPER For prime256v1 aka secp256r1 this is: These can be created e.g. Usually it is NATO phonetic alphabet. Ask a new question Source code dCode retains ownership of WebThis Cipher Identifier Tool will help you identify and solve other types of cryptograms. Write to dCode! a bug ? WebThis Cipher Identifier Tool will help you identify and solve other types of cryptograms.
Tag(s) : Cryptography, Cryptanalysis, dCode. For that, NCID uses several multiple neural networks from which you can select one or more. cipher_identifier does not have a standard license declared. This tool will help you identify the type of cipher, as well as give you Text Analysis Tool Example: Encrypt DCODE with the keys A=5, B=3 and the English/latin alphabet ABCDEFGHIJKLMNOPQRSTUVWXYZ. CrypTool-Online (CTO for short) offers applications for testing, learning and discovering old and modern cryptography. Caesar cipher is best known with a shift of 3, all other shifts are possible.
My Gila River Memorials,
Importance Of Making Travel Arrangements Accurately For Customers,
Florida Toll Roads Suspended,
Grace Thorpe,
Articles D

 The NEW Role of Women in the Entertainment Industry (and Beyond!)
The NEW Role of Women in the Entertainment Industry (and Beyond!) Harness the Power of Your Dreams for Your Career!
Harness the Power of Your Dreams for Your Career! Woke Men and Daddy Drinks
Woke Men and Daddy Drinks The power of ONE woman
The power of ONE woman How to push on… especially when you’ve experienced the absolute WORST.
How to push on… especially when you’ve experienced the absolute WORST. Your New Year Deserves a New Story
Your New Year Deserves a New Story

